OpenID Connect
OpenID Connect (OIDC) is an identity layer that sits on top of the OAuth 2.0 protocol for the purpose of authenticating users needing to access protected APIs. OIDC does not provide authorization; that is handled by an OAuth 2.0 flow that presents the authenticated identity to an authorization server. In OIDC, the mechanism for delivery of the identity information is a security token, known as an "ID Token." The ID Token contains authentication claims about a user as a JSON Web Token (JWT). When delivered by EmpowerID, the claims payload is an ID Token that looks similar to that shown below. Note that more or less claims could be in the token.
{
"iss": "EmpowerID",
"sub": "khmcclure",
"aud": "5c168a71-d47b-4321-bdba-648984e99521",
"iat": 1597961104,
"nbf": 1595282704,
"exp": 1600639504,
"oid": "9b592c74-c014-4536-bfac-f706a4c8d89f",
"name": "Kris McClurring",
"email": "kris.mcclurring@eiddocs.onmicrosoft.com",
"azp": "5c168a71-d47b-4321-bdba-648984e99521",
"at_hash": "EJ04K1puK2OfKrouc_7t_g",
"c_hash": "3sEvqXZmp2hillFqkfwEZg",
"jti": "66054b39-9ce2-49be-88b4-b1bd0aa39bfa"
}
The definition of the claims in the above token are as follows:
| Claim Type | Value | Description |
|---|---|---|
iss | EmpowerID | Identifies the entity that issued the token. See OAuth 2.0 Authorization framework, section 4.1.1 for more information about this claim type. |
sub | khmcclure | Identifies the principal that is the subject of the token. See OAuth 2.0 Authorization framework, section 4.1.2 for more information about this claim type. |
aud | 5c168a71-d47b-4321-bdba-648984e99521 | Identifies the recipients for which the token is intended. See OAuth 2.0 Authorization framework, section 4.1.3 for more information about this claim type. |
iat | 1597961104 | Identifies the time EmpowerID issued the token. See OAuth 2.0 Authorization framework, section 4.1.6 for more information about this claim type. |
nbf | 1595282704 | Identifies the time before which the token MUST NOT be accepted for processing. See OAuth 2.0 Authorization framework, section 4.1.5 for more information about this claim type. |
exp | 1600639504 | Identifies the expiration time on or after which the token MUST NOT be accepted for processing. See OAuth 2.0 Authorization framework, section 4.1.4 for more information about this claim type. |
oid | 9b592c74-c014-4536-bfac-f706a4c8d89f | Person GUID that uniquely identifies the subject of the token in EmpowerID. |
name | Kris McClurring | Full name of the token subject. |
email | kris.mcclurring@eiddocs.onmicrosoft.com | Email address of the token subject registered in EmpowerID. |
azp | 5c168a71-d47b-4321-bdba-648984e99521 | The authorized party to whom the token was issued. |
at_hash | EJ04K1puK2OfKrouc_7t_g | Access token hash value. Used to provide validation that the access token is tied to the identity token. |
c_hash | 3sEvqXZmp2hillFqkfwEZg | Authorization code hash value. Used to provide validation that the authorization code is tied to the identity token. |
jti | 66054b39-9ce2-49be-88b4-b1bd0aa39bfa | GUID that uniquely identifies the token. See OAuth 2.0 Authorization framework, section 4.1.7 for more information about this claim type. |
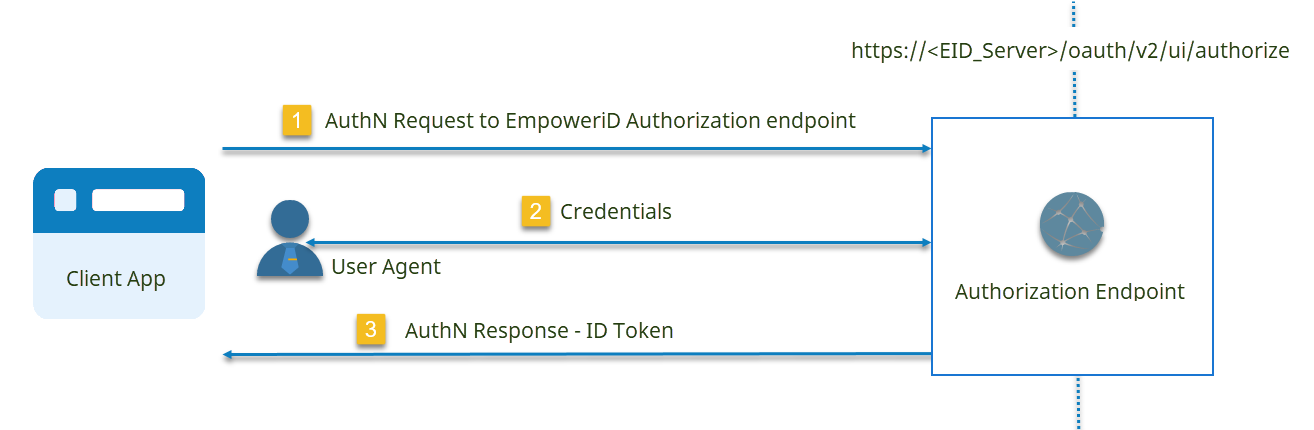
The sequence for authenticating using OIDC looks like that shown in the following image. As OIDC is used in OAuth 2.0 flows, the image is incomplete in that it only depicts the authentication stage of the flow. A more complete presentation of what occurs when using OpenID Connect in an OAuth 2.0 grant in EmpowerID is shown in the OAuth 2.0 Authorization Code Grant.